In this article, we will discuss the User Secrets feature in Asp.Net Core. This article describes techniques for storing and retrieving private information like databases, passwords, API Keys, etc.. while building an ASP.NET Core application on a development machine. While dealing with ASP.NET web applications, you'll want to protect specific application data that shouldn't be shared with others, known as user secrets. A database connection string that also includes the user ID and password for the database may be one of your user secrets. You might also want to avoid disclosing information like connection details, API keys, and access keys. Generally, all this information is mentioned in the configuration like appsettings.json and we usually push or check-in those files as well to our Version Control like GIT, TFS, etc…. but it’s not good practice to push your application secrets to version because someone can steal those secrets data and can cause harm to your application.
When you're developing websites and web APIs using ASP.NET Core, you often have passwords, API keys, and other secrets you wish to keep away from prying eyes. It may be devastating to include these secrets in a configuration file like appsettings.json and unintentionally push those files to a Git repository. Microsoft offers a secret manager tool that for development reasons, maintains private information in a separate secrets.json file on your development computer that is accessible by ASP.NET Core's built-in configuration builder. As such, you can avoid accidentally adding these secrets to your Git repository by not including them in your configuration files.
Configuration in Asp.Net core:
ASP.NET Core provides a built-in way to manage user secrets that allows you to store sensitive information such as API keys, connection strings, and other application secrets outside of your code repository. In ASP.NET Core, managing user secrets involves storing sensitive information such as API keys, connection strings, and other credentials outside of your codebase, and accessing them during development without exposing them to other users or developers.
Add user secrets management :
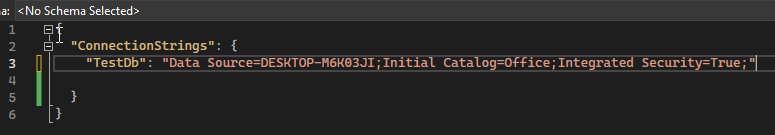
Let’s imagine that we have our secret data and ApiKey in the “appsettings.json” file, and we want to put it in the user secrets.

Once you will create your project this is how your project will appear on the right side in the Solution explorer window.
It's simple to include user secrets management into your project. All you need to do is select the project in the Solution Explorer window, right-click on the project, and then select “Manage User Secrets”, as illustrated in Figure below.
Step1:
This will create or open the secrets.json file for your project. All you need to do is just copy the secret data of appsetting.cs file into a secret.json file as shown in the below picture.
Step:2
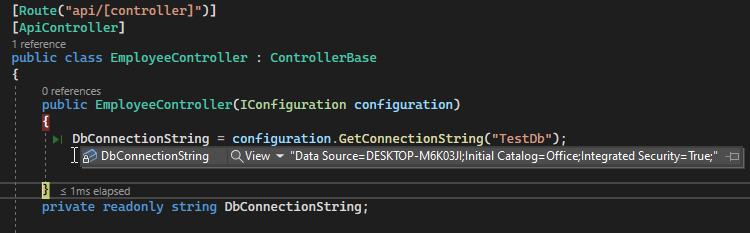
Once we start executing or running the code it is accepting the data of secret.json, As you can see give below is a screenshot showing the actual data acceptance of secret.json in the controller.
Note: when we create the file “secrets.json” this is created outside of the solution and, the hash is added into .csproj, as shown in the following images.
The folder where
secrets.json is created.
Once we create the manage user secret file and If we want to change anything in appsettings.json then it won’t affect in secret.json file but remember if the key doesn’t match of secret.json file and the same key in the appsetting.json file then by default it will pick the data of appsettings.json file. Look at the picture given below for a better understanding.

Why should use User Secrets Manager?
Normally, settings are stored in the "appsettings.json" file, but there are some settings, like passwords, that we don't want to disclose. In order to ensure that these settings are only available on our machine, we employ user secrets. During the creation of an ASP.NET Core project, sensitive data is stored in the Secret Manager tool. A sensitive piece of information is an app secret in this situation. App secrets are kept apart from the project tree in a different place. App secrets may be shared between numerous projects or connected to one particular project.
Conclusion:
A secret manager tool provided by Microsoft enables one to save secrets (in plain text) on the local development Computer so that they are accessible locally while developing applications. Any settings found in appsettings.json and appsettings.environment.json are replaced with these secrets. User secrets are a great alternative to environment variables. The structure in secrets.json matches the one we already have in appsettings.json and is in my opinion a great tool to administrate secrets for each developer.
I genuinely hope you enjoyed reading this article and found something useful. Comment below with your thoughts and recommendations.

Share This Post
Support Me